The Quantum Frontier (Part 2): The 'Crypto-Apocalypse': Why Shor's Algorithm Makes Your Data Obsolete
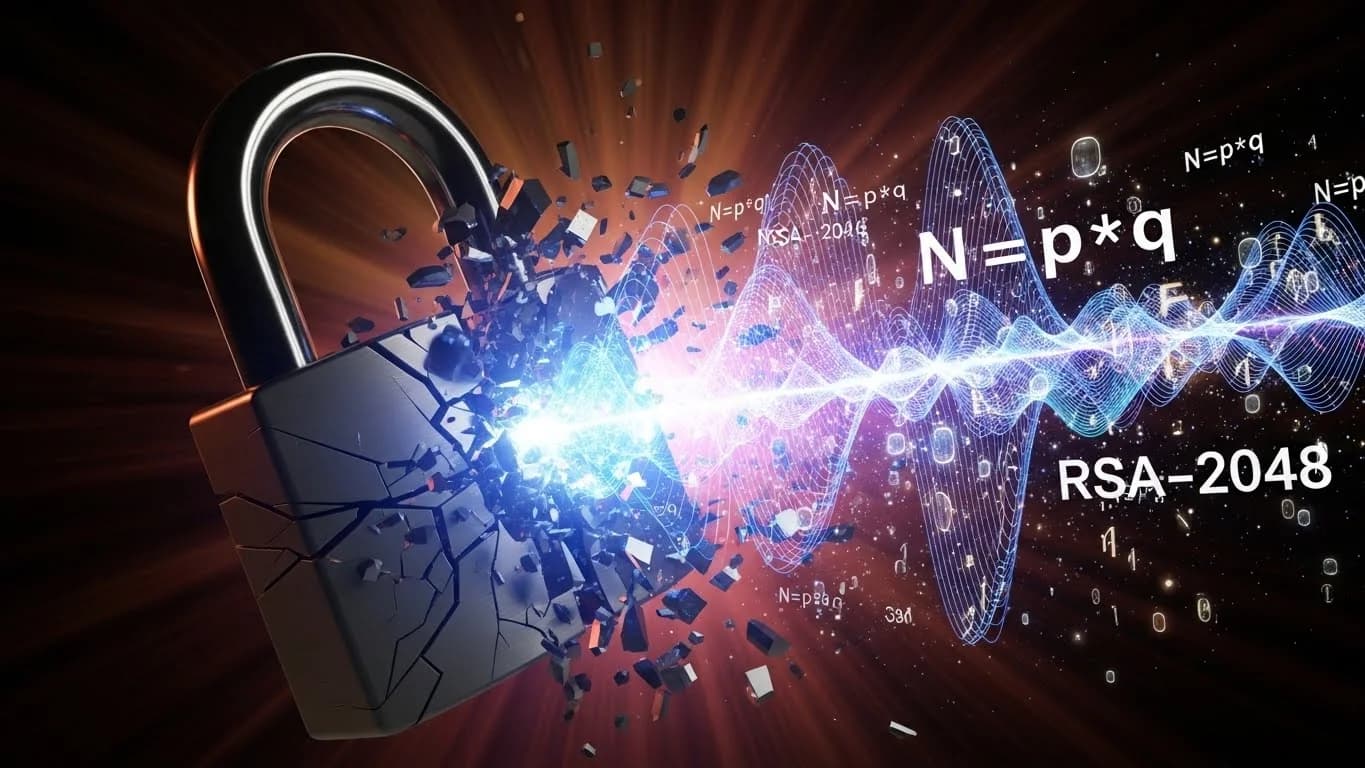
Table of Contents
- The Mathematical Wall Protecting Your Data
- Peter Shor's Quantum "Cheat Code"
- How Shor's Algorithm Actually Works (The Concept)
- The Threat is Now: 'Harvest Now, Decrypt Later'
- Conclusion
The Mathematical Wall Protecting Your Data
Modern security relies on the hardness of prime factorization (RSA) and discrete logs (ECC). Classical computers cannot feasibly reverse these operations at large key sizes.
Peter Shor's Quantum "Cheat Code"
In 1994, Peter Shor introduced a quantum algorithm that factors large integers in polynomial time on a fault-tolerant quantum computer, collapsing the security assumptions of RSA/ECC.
How Shor's Algorithm Actually Works (The Concept)
Shor reduces factoring to period finding and leverages the Quantum Fourier Transform (QFT) to extract periodicity—revealing factors efficiently.
The Threat is Now: 'Harvest Now, Decrypt Later'
Adversaries are exfiltrating encrypted data now to decrypt later once hardware catches up.
Conclusion
Shor's Algorithm turns our "impossible" problem into a tractable one for quantum machines—the clock is ticking.